Key Takeaways:
- Understand the basics of Zero Trust Network Access (ZTNA) and its importance in modern cybersecurity.
- Learn about the challenges faced by traditional security models and how ZTNA addresses them.
- Get insights into the implementation process of ZTNA and the best practices to follow.
Introduction to Zero Trust Network Access (ZTNA)
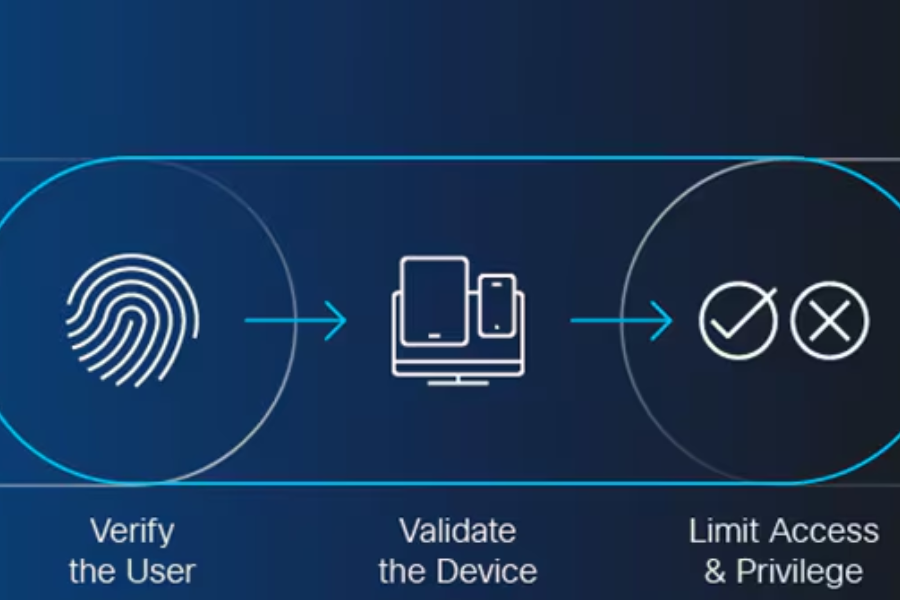
Zero Trust Network Access (ZTNA) significantly shifts from conventional security paradigms. Rather than assuming that internal network traffic is safe, ZTNA embodies the principle of “never trust, always verify.” This security approach safeguards against unauthorized access by continuously authenticating and authorizing all users and devices. In an era where cybersecurity threats are more prevalent and sophisticated, ZTNA stands out as a robust solution. For those wondering what is ZTNA, it is a methodology designed to fortify an organization’s cybersecurity framework by mitigating the inherent risks within traditional security models.
ZTNA’s proactive stance against potential threats makes it a cornerstone concept for any organization aiming to protect its network assets comprehensively. It eliminates the false sense of security provided by traditional perimeter-based security strategies, which often crumble under advanced and persistent cyber-attacks. By implementing ZTNA, organizations can maintain higher security integrity, ensuring that sensitive data and resources remain protected against breaches.
Challenges with Traditional Security Models
Traditional security mechanisms primarily rely on perimeter defenses, distinguishing between what’s considered ‘trusted’ inside the network and ‘untrusted’ outside. However, this model poses several challenges:
- Increased Remote Work: The surge in remote work blurs the boundaries of traditional network perimeters, making it difficult to adequately secure all access points. Employees access the network from various locations and devices, introducing multiple potential vulnerabilities. This trend has intensified with the rise of remote and hybrid work models, necessitating more flexible security solutions.
- Advanced Threats: Sophisticated cyber threats can bypass perimeter defenses, gaining unauthorized access and causing significant damage. Attackers often exploit weak points within the network, and once inside, they can move laterally, accessing sensitive information. Traditional models need help to detect and respond to such advanced threats effectively.
- Cloud Adoption: The widespread adoption of cloud services requires more dynamic and flexible security strategies, which traditional models need help to provide. Organizations migrating their data and applications to the cloud need security solutions to handle diverse and dispersed environments. Traditional security models often must address the complexities of extensive cloud use.
How ZTNA Addresses These Challenges
ZTNA takes a holistic and adaptive approach to overcome the shortcomings of conventional security models:
Continuous Verification
ZTNA continuously verifies the authenticity of users and devices before granting access to network resources. This real-time verification significantly reduces the risk of unauthorized access. Instead of assuming trust based on network location or previous behavior, each access attempt is independently authenticated and assessed for potential danger. By verifying every access request, ZTNA ensures that only legitimate users and devices can interact with the network, enhancing overall security.
Microsegmentation
By segmenting the network into smaller, isolated zones, ZTNA limits the lateral movement of potential threats. This means that even if one part of the network is compromised, the breach can be contained without affecting other areas. Microsegmentation ensures that critical assets are compartmentalized and protected individually. This granular level of control prevents attackers from gaining wide-reaching access to sensitive data and systems, significantly mitigating the impact of breaches.
Adaptive Security Policies
ZTNA employs adaptive security policies that adjust based on real-time risk assessments. This dynamic approach enables organizations to respond effectively to emerging threats. Security policies are not static; they evolve as new threats and vulnerabilities are understood, ensuring the organization’s defenses remain robust. Adaptive policies allow for quick and efficient responses to changing threat landscapes, enhancing the resilience of the security framework.
Implementing ZTNA: Best Practices
For a successful ZTNA implementation, consider the following best practices:
Assess Current Security Posture
Begin by conducting a thorough assessment of your existing security measures. Identifying gaps and vulnerabilities will help you understand where ZTNA can add value. This assessment should cover all aspects of your network infrastructure, including remote access points, cloud services, and internal systems. By clearly understanding your current security posture, you can effectively tailor your ZTNA implementation to address specific vulnerabilities.
Choose the Right ZTNA Solution
Select a ZTNA solution that aligns with your organization’s needs and infrastructure. Ensure it provides comprehensive coverage and can integrate seamlessly with your current systems. Consider factors such as scalability, ease of deployment, and the ability to support diverse user environments. A well-chosen ZTNA solution can provide robust security without disrupting your organization’s operations, leading to a smoother and more effective implementation process.
Train Employees
Employee training is crucial for the effective implementation of ZTNA. Educate your staff on the new security protocols and practices, ensuring they understand the importance of adhering to them. Regular training sessions and updates reinforce the significance of maintaining security standards. Empowering employees with knowledge about ZTNA enhances the overall security culture within the organization, reducing the likelihood of user-related security breaches.
Monitor and Adapt
Continuous monitoring and adaptation are vital. Review the effectiveness of your ZTNA implementation regularly and make necessary adjustments to keep up with evolving threats. Use analytics and threat intelligence to stay informed about new risks and refine your security policies accordingly. By maintaining a proactive approach to monitoring and adaptation, organizations can ensure that their ZTNA implementation remains resilient and effective in the face of changing cybersecurity threats.
Conclusion
Zero Trust Network Access (ZTNA) is an essential advancement in cybersecurity, offering a robust solution to the deficiencies of traditional security models. ZTNA provides a comprehensive approach to safeguarding network resources by continuously verifying access and implementing adaptive security measures. Organizations that embrace ZTNA can enhance their security, improve operational efficiency, and better protect their sensitive data in an increasingly interconnected world.
The transition to ZTNA represents not just an upgrade in technology but a fundamental shift in how organizations think about and implement security. It underscores the importance of vigilance and adaptability in the face of ever-evolving cybersecurity threats. As businesses and institutions navigate the complexities of modern digital landscapes, ZTNA offers a pathway to more resilient and effective security practices.
Stay in touch to get more updates & news on Nycitypaper !